In Cryptographic Terms What Does Cipher Indicate
Cryptography is the art and science of making data impossible to read. 1The encrypted data 2Both the.

Art Of Cryptography Txt In Cryptographic Terms What Does Cipher Indicate The Algorithm Used For Encryption And Decryption Secret Key Cryptography Is Course Hero
The ciphertext should be different since a different key was used.

In cryptographic terms what does cipher indicate. In cryptographic terms what does cipher indicate -- Algorithm for performing encryption and decryption. Here we have a set of multiple-choice questions and answers quiz on ciphers in Cryptography basic concepts of Cryptography Techniques and different types of ciphers. A cipher is a method of hiding words or text with encryption by replacing original letters with other letters numbers and symbols through substitution or transposition.
An idea in cryptography that all codes and ciphers aim for perfect secrecy means that the cipher is truly unbreakable. A monoalphabetic substitution cipher where graphical symbols are used. In cryptographic terms what does cipher indicate.
21 A generalization of the Caesar cipher knows as the affine Caesar cipher has the following form. In which of the following cryptographic methods is the order of the units in the data rearranged to form the ciphertext. One of these tools is the Symmetric Key Encryption where the key used for encryption and decryption is the same.
If that same message A were encrypted with key B the result should not be ciphertext Y. 3The algorithm used for encryption and decryption. In cryptographic terms what does cipher indicate.
1In cryptographic terms what does cipher indicate -- Algorithm for performing encryption and decryption 2. View-10078 Question Posted on 16 Jul 2020 In cryptographic terms what does cipher indicate. It divides the input into predefined lengths and pads the remainder to maintain a set length When you get an SSL certificate from a web page.
Message A was encrypted with key A and the result is ciphertext Y. Malleability cryptography is the ability to transform a ciphertext into a different ciphertext which will produce a new and different plaintext when decoded. In the second chapter we discussed the fundamentals of modern cryptography.
In which of the following cryptographic methods is the order of the units in the data rearranged to form the ciphertext. Malleability is generally considered an undesirable property for message. Cryptography is technique of securing information and communications through use of codes so that only those person for whom the information is intended can understand it and process it.
Otherwise decryption is impossible because more than one plaintext character. Cipher also refers to the encrypted text cryptography system or encryption key for the. We equated cryptography with a toolkit where various cryptographic techniques are considered as the basic tools.
What does automorphism indicate in cryptography particularly in plaintext and ciphertext context. What you are referring to could be categorized as a classical pigpen cipher. The cipher generated by combining multiple t.
The task of the various encryption methods is to start with plain readable data the plaintext and scramble it so it becomes an unreadable ciphertext. In cryptography ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm called a cipher. Claude Shannon devised the idea that a piece of cipher text is perfectly secret if it provides no information about the original plaintext.
In cryptography a cryptosystem is said to be semantically secure if it is computationally infeasible for an attacker to extract any knowledge of the plaintext based on the ciphertext and its length. A block cipher is so-called because the scheme encrypts one fixed-size block of data at a time. 1 You are supposed to use hill cipher for encryption technique.
Cryptography is the study and practice of techniques for secure communication in the presence of third parties called adversaries. I know what an automorphism is in mathematical sense - an isomorphism from G to G itself. That is if p q then Ek p Ek q.
Submitted by Monika Sharma on February 02 2020. C Ea b p ap b mod 26 A basic requirement of any encryption algorithm is that it be one-to-one. But if the ciphertext is the same this occurrence is referred to as key clustering.
In a block cipher a given plaintext block will always encrypt to the same ciphertext when using the same key ie it is deterministic whereas the same plaintext will encrypt to different ciphertext in a stream cipher. It deals with developing and analyzing protocols which prevents malicious third parties from retrieving information being shared between two entities thereby following the various aspects of information security. How does a block cipher handle plaintext input.
In which of the following cryptographic methods is the order of the units in. Monoalphabetic Substitution Cipher. Answer 1 of 3.
You might change the symbols and maybe even the way you encode things but replacing text with symbols will always boild down to a simple monoalphabetic substitution cipher. Show More 1In cryptographic terms what does cipher indicate -- Algorithm for performing. Choose the correct option from below list 1The e.
Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. The prefix crypt means hidden and suffix graphy means writing. For each plaintext letter p substitute the ciphertext letter C.
A combination of substitution and transposition is also often employed. I read a research paper in which the writer again and again writes about norm preserving automorphism such as ϕ a a. Cryptography and its Types.
Some encryption schemes such as RSA without encryption padding and many block ciphers used in Electronic Codebook ECB mode or block ciphers with a constant. Automorphism in Cryptography. -- transposition ciphers 3.
Thus preventing unauthorized access to information. -- transposition ciphers 3.

Definition Of Cryptography Pcmag

Art Of Crypto Txt 1 In Cryptographic Terms What Does Cipher Indicate Algorithm For Performing Encryption And Decryption 2 In Which Of The Following Course Hero

Art Of Crypto Txt 1 In Cryptographic Terms What Does Cipher Indicate Algorithm For Performing Encryption And Decryption 2 In Which Of The Following Course Hero

Art Of Crypto Txt 1 In Cryptographic Terms What Does Cipher Indicate Algorithm For Performing Encryption And Decryption 2 In Which Of The Following Course Hero

Art Of Crypto Txt 1 In Cryptographic Terms What Does Cipher Indicate Algorithm For Performing Encryption And Decryption 2 In Which Of The Following Course Hero

Runes Poster A4 Size Wicca Pagan Witch Goth Book Of Shadows Runes Norse Runes Book Of Shadows

Cryptology Vigenere Ciphers Britannica

Cryptography In The 16th Century A Nomenclator Combines A Substitution Cipher With A Small Code Set As In Th Mary Queen Of Scots Cryptography Writing Systems

Art Of Crypto Txt 1 In Cryptographic Terms What Does Cipher Indicate Algorithm For Performing Encryption And Decryption 2 In Which Of The Following Course Hero
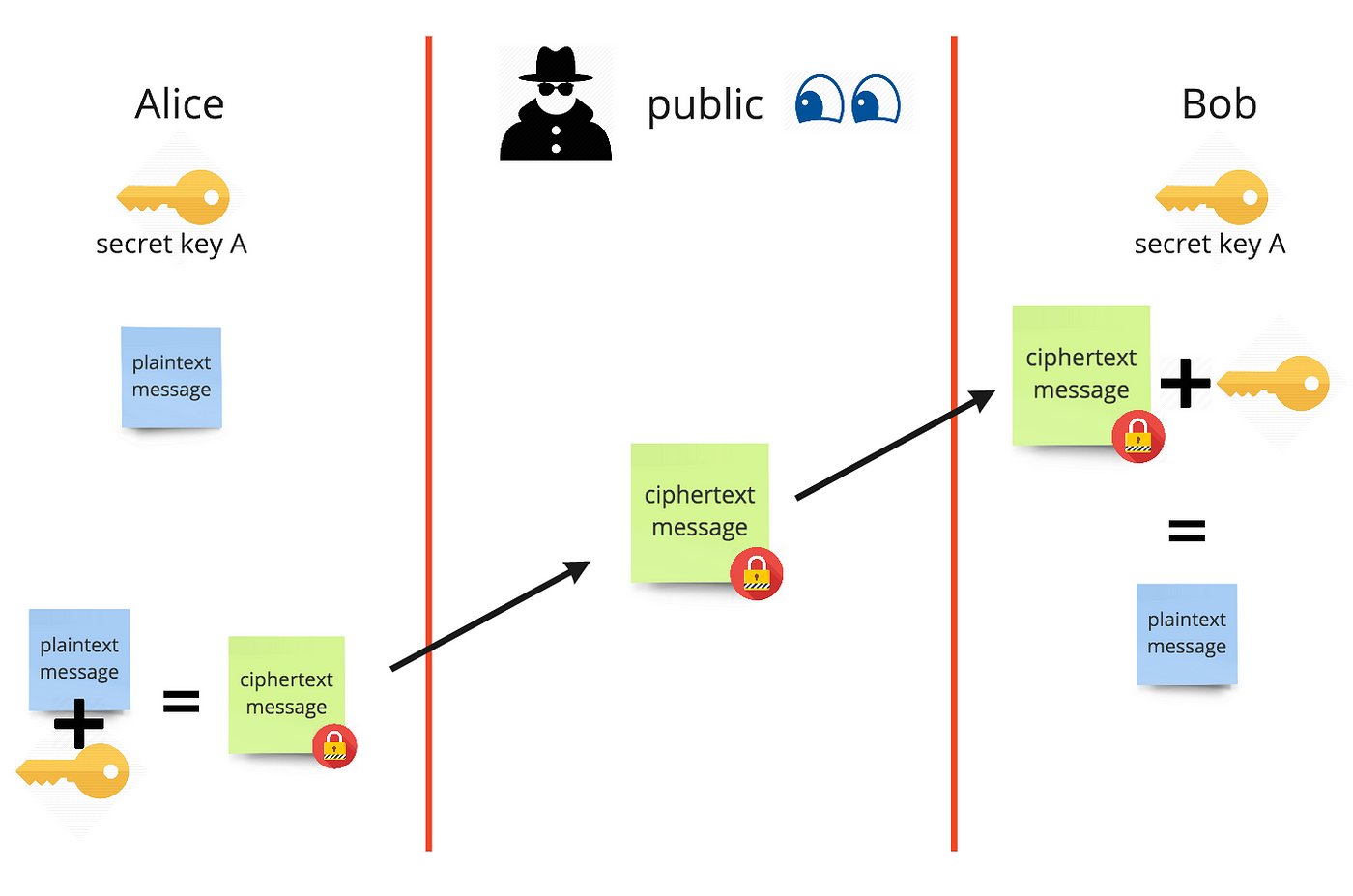
What Are Encryption Keys And How Do They Work By Dominic Fraser Codeclan Medium

Art Of Crypto Txt 1 In Cryptographic Terms What Does Cipher Indicate Algorithm For Performing Encryption And Decryption 2 In Which Of The Following Course Hero

Fear Of Missing Out Fomo In 2021 Fear Fomo Fear Of Missing Out

Art Of Crypto Txt 1 In Cryptographic Terms What Does Cipher Indicate Algorithm For Performing Encryption And Decryption 2 In Which Of The Following Course Hero

The Braille Alphabet And Japanese Braille Syllabics Tenjis158 Font Created By Kasai Hakuh Braille Alphabet Braille Alphabet
Posting Komentar untuk "In Cryptographic Terms What Does Cipher Indicate"