Crypto-6-ikmp_policy_default Using Isakmp Default Policies
There are eight default ISAKMP default policies supported see the table below. Processing of GDOI mode failed with peer at 10081.
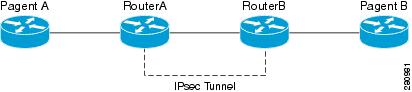
Ipsec Management Configuration Guide Cisco Ios Xe Release 3s Ipsec Usability Enhancements Support Cisco
We have a number of Cisco 2911s and 2811s using this authentication method RSASIG successfully.

Crypto-6-ikmp_policy_default using isakmp default policies. Crypto key generate rsa general-keys modulus 2048 label VPN-client exportableAdd this command to use PKI instead of a preshared key as the authentication. GDOI-Server configrouter ospf 1 GDOI-Server config-routerrouter-id 7777. Verify the Site-to-Site IPsec VPN Configuration.
Router configure terminal Step 3 OptionalTurnsoffdefaultISAKMPpolicieswith priorities65507-65514. Please issue a view command to see it Jul 15 2016 163434878 BRST. Processing of Main Mode failed with peer at1721617234 Access-list mismatch -If the access-lists on the peer IPSEC devices do not match that is if they are not mirror images of each other then the following error will occur.
IKE packet from 102502425 was not encrypted and it shouldve been. ISAKMP is ON. Previously you used the show crypto isakmp policy command to display the configured ISAKMP policies on the.
I created a group provided a pre-shared key. No crypto isakmp default policy. Crypto isakmp policy 21 encr 3des authentication pre-share group 2 lifetime 3600 crypto isakmp key fcnfkfdbckf address 19458681 crypto isakmp key fcnfkfdbckf address 194583625 crypto isakmp key Remotekeyagent address 939598104.
Processing of Informational mode failed with peer at 62160XXXXXX. The command no crypto isakmp default policy was intriduced in 12420T. We wish to interface a OpenSWAN configuration to a Cisco 2911 however despite trying a number of configurations none appear to work.
We have tested 2911 to 2911 successfully and then switched out a 2911. Match statements to FVRF and the local address are optional. Processing of Informational mode failed with peer at 10111 Jul 8.
Before we start with the fun stuff well need to set up the basic connectivity and it will be very basic. Crypto isakmp policy 5. Jan 28 041054138.
Routershow run sec crypto. Multiple ISAKMP policies can be configured each with a unique priority number 1 to 10000. Crypto isakmp key cisco123 address 0000.
Sep 19 122943035. Using ISAKMP Default policies Verifying Default IPsec Transform-Sets. Step4 Routerconfig no crypto isakmp default policy Examples.
Router show crypto isakmp default policy configureterminal Entersglobalconfigurationmode. Encryption aes 256Use show run all to see the authentication rsa-sig line. Ip route 17229300 2552552550 1723020252.
IKE policy configuration These parameters are used during negociation. Crypto isakmp key cisco123 address 200112. Verify the IPsec configuration on R1 and R3.
Crypto pki token default removal timeout 0. Step3 Router configure terminal OptionalTurnsoffdefaultISAKMPpolicieswith priorities65507-65514. Using ISAKMP Default policies Jul 15 2016 163434554 BRST.
A transform set represents a certain combination of security protocols and algorithms. Using ISAKMP Default policies Jul 8. New SMS received on index 4.
ISAKMP is ON. Routerconfig no crypto isakmp default policy Step 4. Crypto isakmp policy 20 encr 3des authentication pre-share group 2 lifetime 28800.
If you have neither manually configured ISAKMP policies with the crypto isakmp policy command nor issued the no crypto isakmp default policy command IPsec will use the default ISAKMP policies to negotiate IKE proposals. Youve obviously got to get a route from server to client such as adding on R2. Proxy identities not supported ISAKMP.
Bonjour Lerreur en entier cest ça. The first is the ISAKMP client group. Crypto isakmp policy 10 DEFAULT ENCRYPTION IS DES AND SHA-1 HASH NOT SHOWN IN THE CONFIG authentication pre-share group 5.
Dadresse comme ci-dessus. Jun 5 182022383. IKE default policy was matched and is being used.
This command defines the majority of the client configuration and. The negociations purpose is to establish an ISAKMP peering between two IPsec endpoints. Enters global configuration mode.
More secure policies should have lower priority numbers. The default IKEv2 policy is used only if there are no user-defined IKEv2 policies. 151-4M6 does have this command.
Crypto ikev2 policy IKEv2-POLICY match fvrf any proposal AES-GCM256-SHA512-DF21. Im trying to set up an 1811 Cisco router to accept VPN connections. As a result GMs will re-register with their KSs just before the expiry of their TEKKEK.
Hi All We use a X509 PKI for authentication of our IPsec VPNs. CISCO 2811 VPN FAIl CRYPTO-6-IKMP_MODE_FAILURE. After the registration the Group Members should have the latest policies and keys including the new RSA keys.
Much of the configuration will be the same as we have seen before ISAKMP policies transform sets IPSec profiles but some will be quite new GDOI groups. If you have neither manually configured ISAKMP policies with the crypto isakmp policy command nor issued the no crypto isakmp default policy command IPsec will use the default ISAKMP policies to negotiate IKE proposals. Crypto isakmp policy 10 encr aes 256 hash sha512 authentication pre-share group 14 crypto ipsec transform-set TS esp-aes 256 esp-sha-hmac Routes.
Routerconfig no crypto isakmp default policy. Router show crypto isakmp default policy Optional Displays default ISAKMP policies if no policy with a priority of 1-10000 is configured. The following is an example system log message that is generated whenever the default ISAKMP policies are in use.
Je veux faire un client pour un routeur Cisco existant. Router show crypto isakmp default policy Step 2 configureterminal Entersglobalconfigurationmode. This is created using the command.
Look for crypto isakmp default policy section int he following doc. Processing of Aggressive mode fa by spicehead-o3ys2 on Oct 24 2019 at 2047 UTC 1st Post. Jul 15 2016 163434510 BRST.
The security association will be made up from the lowest. I try to connect with my PC XP using Cisco VPN Client but at the hypterminal window I see the message. There are eight default ISAKMP default policies supported see the table below.
If you use FVRF include match fvrf statement into your profile. R4 R4sh ip int bri e unas Interface IP-Address OK. Interface Cellular 0.

Cara Main Crypto Idx Like And Share

Cara Main Crypto Idx Like And Share

Cara Main Crypto Idx Like And Share

Solved How To Disable Isakmp Default Policy On Cisco 2800 Router Cisco Community
Cara Main Crypto Idx Like And Share
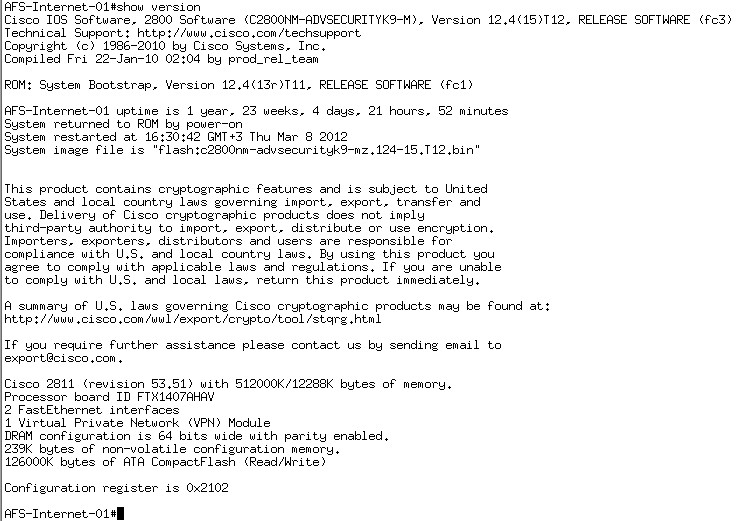
Solved How To Disable Isakmp Default Policy On Cisco 2800 Router Cisco Community

Cara Main Crypto Idx Like And Share

Cara Main Crypto Idx Like And Share

Cara Main Crypto Idx Like And Share
Cara Main Crypto Idx Like And Share





Posting Komentar untuk "Crypto-6-ikmp_policy_default Using Isakmp Default Policies"