Crypto-4-pkt_replay_err Decrypt Replay Check Failed
In this case anti-replay check failure causes the recipient router to drop packets that are out of order. The disconnection happens two or three times everyday and it comes back by itself in some time 2080 mins not the same.
The User Recieves The Crypto 4 Pkt Replay Err Decrypt Replay Check Failed Error Message With Mul Cisco Community
Crypto ipsec transform-set basic esp-des esp-md5-hmac.
Crypto-4-pkt_replay_err decrypt replay check failed. Because of the anti-replay check failure these packets are dropped on the receiving router. The device is a Cisco 1812 with the IOS version c181x-advipservicesk9-mz124-15T13bin. VPN Randomly Disconnecting between Cisco and Azure.
We regularly see replay errors. A site to site VPN between a Cisco 2951 router and Azure is set up. The disconnection happens two or three times everyday and it comes back by itself in some time 2080 mins not the same.
Crypto isakmp key cisco123 address 1921652012. All A site to site VPN between a Cisco 2951 router and Azure is set up. Then you telnet to assuming the port youre coming in on can somehow reach vlan 1.
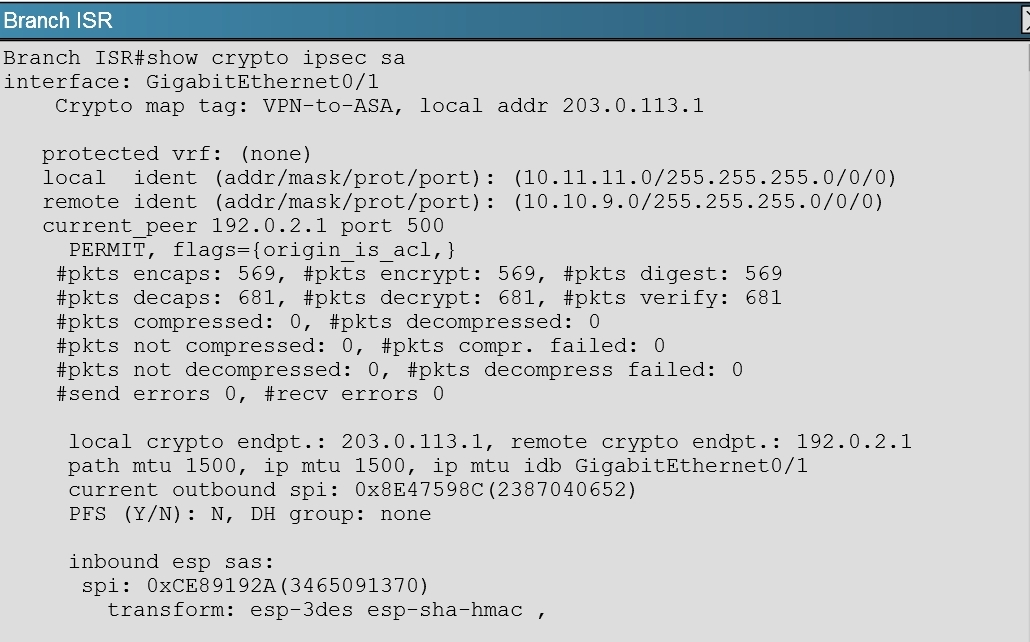
Line vty 0 4. My_pseudotime is 60000678 secs peer_pseudotime is 50003334 secs replay_window is 100 second Feb 10 210156043. Reagrding the show crypto ipsec sa I forwarded you the output of that command.
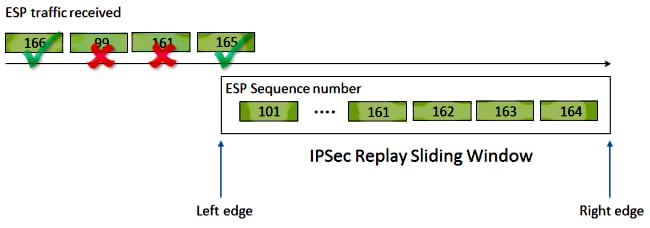
Replay Check Failure Description IPSec provides anti-replay protection against an attacker who duplicates encrypted packets with the assignment of a monotonically increasing sequence number to each encrypted packet. Out of these the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. Show crypto ipsec sa This command shows IPsec SAs built between peers.
Cisco IPSec authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence number to each encrypted packet2E Security association SA anti-replay is a security service in which the receiver can reject old or duplicate packets to protect itself against replay. You can also read the IPSEC charter on the ietf website to know the significance This msg can come when there is a delay in the network path and the packets are fragmented. This symptom is observed when a multipoint GRE mGRE and IPSec tunnel is built between two routers.
The tunnel came up once it was configured but it had random disconnection every day. Because of this delay the anti. My IOS version.
If its ssh then you need to configure other stuff as per ragzillas post also need to set the switchs domain name generate crypto keys. Example The following example shows that anti-replay checking is disabled for IPsec connections to 172171502 but enabled and the default window size is 64 for IPsec connections to 172171503 and 172171504. Commands that I have used so far like show crypto isakmp sa and show crypto ipsec sa do not show connection ids that match the value logged in the message.
The problem lies in router behavior not in the configuration it has been discussed at. Expanding and Disabling of an Anti-Replay Window for a Particular Crypto Map Dynamic Crypto Map or Crypto Profile. So I have this log message from a Cisco router.
Please read more about it on google if you are interested. My_pseudotime is 60000678 secs peer_pseudotime is 50003334 secs replay_window is 100 second Feb 10 210156043. Because of the anti-replay check failure these packets are dropped on the receiving router.
This scenario results in the failure of anti-replay checks. Crypto ipsec security-association replay window-size 1024. Replay check failed Cisco IPsec authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence number to each encrypted packet.
Ip address. Each of the spokes is connected to the 3945s over VTI tunnels three and four. Replay check failed you can try changing the transform set for that tunnel so that it doesnt use any hashing algorithm MD5SHA.
The tunnel came up once it was configured but it had random disconnection every day. This symptom is observed when a multipoint GRE mGRE and IPSec tunnel is built between two routers. This website uses cookies to improve your experience while you navigate through the website.
Replay check failed connection id777 sequence number218932. Hi Wen Thanks for your prompt feedback. Replay timer has expired.
Anti-replay is a security service in which the receiver can reject old or duplicate packets in order to protect itself against replay attacks. Crypto ipsec security-association replay window-size 128 なおwindow-sizeのデフォルトが64なので64以上に増やして調整を行う事となります 64を基点に倍にしていきます641282561024 ログを毎日チェックするような事でもなければまず気付かないエラーですね. Interface FastEthernet00 ip address 19216811 2552552550.
Apr 22 114805949. I have a pair of 3945E routers I use as redundant VPN head-ends in our data center and numerous 2901 and one 2951 used as spoke routers. Whats the default setting for keepalive and dpd.
The encrypted tunnel is built between 12111 and 12112 for traffic that goes between networks 20110 and 10110. Crypto map mymap 10 ipsec-isakmp set peer 1921652012 set transform-set basic match address 101. The Anti Replay has a major significance in crypto world.
Ipsec Anti Replay Check Failures Cisco
Q 93719 What Is The Most Likely Cause Of This Error

Replay Check Failed On Cisco Router With Ipsec Asa Me2
300 209 Exam Free Actual Q As Page 26 Examtopics
Crypto 4 Pkt Replay Err Decrypt Replay Check Failed Connection Id Xxx Lostdomain
Understanding Ip Sec Vpn Operation Packetonwire Net
Understanding Ip Sec Vpn Operation Packetonwire Net
Posting Komentar untuk "Crypto-4-pkt_replay_err Decrypt Replay Check Failed"