In Cryptography The Order Of The Letters In A Message Is Arranged By
Cryptography render the message unintelligible to outsiders by various transformations of the text. This is the key that will unlock the coded message later.

Pin By Michael Bailey On White Magic Book Of Shadows Magic Symbols Lettering Alphabet
In cryptography the order of the letters in a message is rearranged by.

In cryptography the order of the letters in a message is arranged by. AnswerIn cryptography the order of the letters in a message is rearranged by transpositional ciphers. None of the mentioned. Cryptography Questions and Answers.
Both a and b D. A simple form of steganography but one that is time consuming to construct is one in which an arrangement of words or letters within an apparently innocuous text spells out the real message. In transposition ciphers the letters are arranged in a different order these ciphers may be.
Both a and b D. When trying to crack a code using by trying all the possibilities this method is known as ____________. Introduction to Cryptography cryptography is the study of secret crypto- writing.
In cryptography the order of the letters in a message is rearranged by. Group letter in pair of two he ll o applying Basic Rules we get pair as he lx lo. Nov 20 2020 0930 AM.
The idea is to encrypt by shifting every letter of the alphabet by a. This matrix therefore yields the ciphertext. Both transpositional ciphers and substitution ciphers.
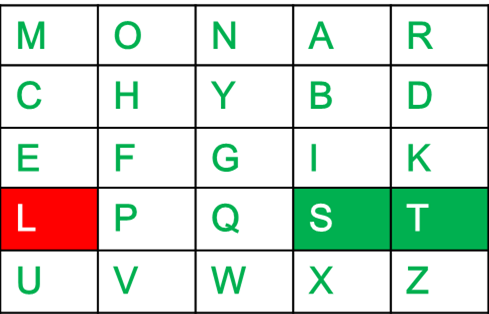
In cryptography the order of the letters in a message is rearranged by _____ A. In cryptography the order of the letters in a message is rearranged by _____ a both transpositional ciphers and substitution ciphers b quadratic ciphers c transpositional ciphers d substitution ciphers. System the letters of the alphabet are arranged to form a 55 grid in which each letter is represented by its row and column number.
Cryptography Questions and Answers. In cryptography the order of the letters in a message is rearranged by _____ Atranspositional ciphersBsubstitution ciphersCboth transpositional ciphers and substitution ciphersDquadratic ciphers. Cryptography Questions and Answers.
Voice privacy in GSM cellular telephone protocol is provided by. Suppose for example that you want to transmit following English version of Pheidippides message to Sparta. In cryptography the order of the letters in a message is rearranged by __________ transpositional ciphers substitution ciphers both transpositional ciphers a quadratic ciphers a 23 What is data encryption standard DES.
The order in which the rows are read out to form the ciphertext is determined by the alphabetical order of the letters in the keyword cat. A _____ cipher occurs when the same letters are used but the order is changed transposition ROT13 is a special case of a Caesar __________ cipher where each character is replaced by a character 13 places later in the alphabet. You code your message by looking at each letter in your message blue and writing down the substitute letter red.
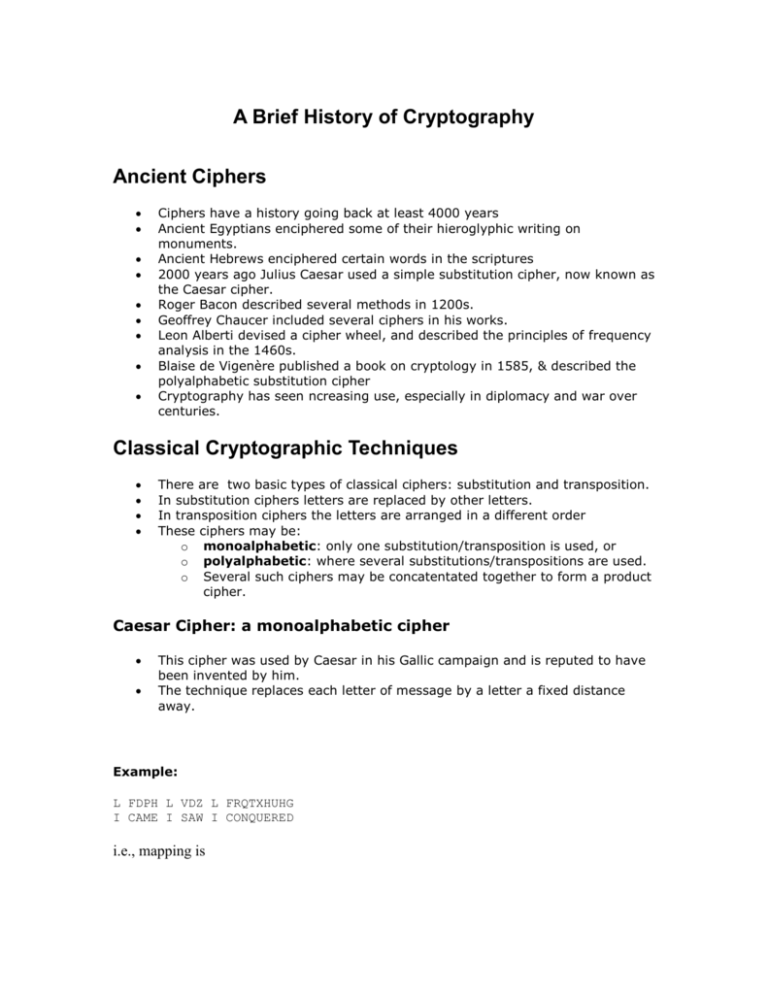
Substitution each letter in the message is replaced with a dierent symbol usually also a letter but the order of the letters remains the same. The simplest example is known as the shift cipher and goes back thousands of years. A monoalphabetic cipher replace each letter of message by a letter a fixed distance away eg use the 3rd letter on reputedly used by Julius Caesar eg.
C both a and b d none of the mentioned. None of the mentioned. L FDPH L VDZ.
In cryptography the order of the letters in a message is rearranged by. Both transpositional ciphers and substitution ciphers. Lo not in the same row and not in the same column of the secret key so by Rule 3 of encryption lo becomes bx.
In cryptography the order of the letters in a message is rearranged byA. The message is usually written without word divisions in rows of letters arranged in a rectangular block. Cryptographic hash function takes an arbitrary block of data and returns.
In cryptography the order of the letters in a message is rearranged by _____. Transpositional ciphers None of the mentioned Both a and b Substitution ciphers. In cryptography the regular characters are called the plaintext and the substitute characters are called the ciphertext.
In cryptography the order of the letters in a message is rearranged by a transpositional ciphers. He in the same row of the secret key so by Rule 1 of encryption he becomes ec. ElGamal encryption system is.
In cryptography the order of the letters in a message is rearranged by _____ Options. Block cipher stream cipher bit cipher byte cipher a 24 A asymmetric-key or public key cipher uses 1 key 2 key 3 key 4 key b. The letters are then transposed in a prearranged order such as by vertical columns diagonals or spirals or by more complicated systems such as the knights tour which is.
AnswerIn cryptography the order of the letters in a message is rearranged by transpositional ciphers. In cryptography the order of the letters in a message is rearranged by A from COMPUTER SCIENCE MISC at DBMS. THE ATHENIANS BESEECH YOU TO HASTEN TO THEIR AID.

Active Directory Certificate Templates 2 Templates Example Templates Example Certificate Templates Active Directory Free Certificate Templates

Pin By Nicole Fraga Pinheiro On Tattoo And Design Zelda Tattoo Writing Alphabet
Encryption Is A Process Of Converting A Message Chegg Com

86 Cryptography Alphabet Re Popular Cryptography Books Gravity Falls Gravity Falls Codes Alphabet Code

Passwords Of The Past World Infographic Cyber Security Technology Hacking Computer Cybersecurity Infographic

Coding Messages Conversation Starters For Couples
A Brief History Of Cryptography

Classical Cryptography B It Cosec
Playfair Cipher With Examples Geeksforgeeks

Playfair Cipher With Examples Geeksforgeeks

The Alan Turing Cryptography Competition Edition 2013 Alan Turing Cryptography Three Letter Words



Posting Komentar untuk "In Cryptography The Order Of The Letters In A Message Is Arranged By"