Cryptographic K-anonymity
XVG is an open-source privacy coin that has a team of international developers. With the help of cryptography the servers and a user jointly determine whether the k-anonymity property holds for the users area without the servers learning any additional information not even whether the property holds.

Si110 Asymmetric Public Key Cryptography
1Cryptographic anonymity strengthens anonymity which only states that identities are not needed at reconstruction but not necessarily hidden 1.

Cryptographic k-anonymity. Crypto-PAnCryptography-based Prefix-preserving Anonymization1 is a cryptographic algorithm for anonymizingIP addresseswhile preserving their subnet structure. Applied Cryptography and Network Security ACNS 2005 Springer-Verlag LNCS 3531 2005. Many studies have been conducted in isolation using different metrics with the consequence that it is not feasible to compare and benchmark the anonymity landscape in a reliable manner across various constructions.
Accumulators from Bilinear Pairings and Applications. Its just mapping the universe of all possible DBs to all those which respect the k-anonymity principle. Xk Yk Zk with the following properties.
Token forgery can be prevented in an electronic cash system as long as the cryptography is sound and securely implemented the secret keys used to sign coins are not compromised and integrity is maintained. As such our work lays the foundation for formalising security models and terminology across a wide range of anonymity notions referenced in the literature while showing how anonymity itself is a surprisingly nuanced concept. Dynamic k-Times Anonymous Authentication.
K-anonymity is a property possessed by certain anonymized dataThe concept of k-anonymity was first introduced by Latanya Sweeney and Pierangela Samarati in a paper published in 1998 as an attempt to solve the problem. Among the now numerous alternative cryptocurrencies derived from Bitcoin Zcash is often touted as the one with the strongest anonymity guarantees due to its basis in well-regarded cryptographic. For any integer λ and any hk Hλ hk is computable in time polynomial in λ.
Privacy Preserving Data Mining k-NN classi- increasingly feeling that they are losing control over their fication Cryptography. An Improved three-factor anonymous Authentication Protocol for WSN s based IoT System Using Symmetric cryptography K Jawad K Mansoor AF Baig A Ghani A Naseem 2019 International Conference on Communication Technologies ComTech 53-59 1 2019. K-anonymity is a lexical transformation on the DB.
Poor values of k or cases when the distance between the original DB and the mapped DB is large can lead to significant privacy leaks. Zcash is the first widespread application of zk-SNARKs a novel form of zero-knowledge cryptography. - Lan Nguyen and Rei Safavi-Naini.
XVG was created back in 2014 under its original name DogecoinDark. With the help of its anonymity tool Tor and its anonymous network layer I2P it is able to hide transactions IP addresses and locations. Such a scheme is called cryptographically anonymous.
Of anonymity in cryptocurrencies and distributed transaction systems irrespective of their implementation. 14 in their work on cryptography from anonymity 3. Cryptographic anonymity strengthens anonymity which only states that identities are not needed at reconstruction but not necessarily hidden.
Monero XMR Monero the title of the most anonymous cryptocurrency. Low-latency anonymity network Use public-key cryptography to establish a circuit with pairwise symmetric keys between hops on the circuit Then use symmetric decryption and re-encryption to move data messages along the established circuits Each node behaves like a mix. It also means that the iden-.
Thus an individual is hidden in a crowd of size k giving her k-anonymity. A user learns whether the k-anonymity property is satisfied and no other information. Thus exactly as you say it is just a property of the DB.
That is the algorithm encrypts any string of bits mathdisplaystyle x mathto a new string mathdisplaystyle E_kx. Prhk HR λx R X kyy R Y kx A1λxyy. Cryptographic solutions have been proposed that will reveal the identity of the multiple spender while preserving user anonymity otherwise.
This model was introduced by Ishai et al. As a result individuals are Keywords. This cryptoart is a collage of the official Monero logo and a photo of Anonymous which I took some years ago.
K-anonymous if for each row in the table there arek 1 other rows in the table that are identical along the quasi-identifier attributes. RSA Confer-ence 2005 Cryptographers Track CT-RSA Springer-Verlag LNCS 3376 pp. Clearly a join with a k-anonymous table would give risek or more matches and create confusion.
Monero literally meaning coin in Esperanto is best known for its privacy and anonymity features which makes it one of the most distinguished privacy coins by obfuscating both the sender the receiver and the amount being sent. Sometimes reconstruction is questionable so the parties that participate in the reconstruction want their identities to remain private. Given person-specific field-structured data produce a release of the data with scientific guarantees that the individuals who are the subjects of the.
For any probabilistic polynomial-time algorithm A. Cryptographic algorithm for anonymizing IP addresses. We refer to 147 for a discussion of cryptographic realizations of an anonymous channel.
The strong privacy guarantee of Zcash is derived from the fact that shielded transactions in Zcash can be fully encrypted on the blockchain yet still be verified as valid under the networks consensus rules by using zk-SNARK proofs. Preprint submitted to Information Processing Letters December 26 2015. We will analyze the most popular crypto projects that allow their users to keep their crypto transactions in secret.
Hkxy hkxy neglλ. Tocurrency anonymity no standardized means are available to evaluate the actual level of privacy achieved by different cryptocurrencies.

Infographic Types Of Cryptography Cryptobuzz Computer Security Cryptography Quantum Computer

The Boom In Crypto Mining Has Created A Shortage Of Graphics Cards And A Spike In Prices Nvidia Stated That They Are Not Ha Graphic Card Crypto Mining Graphic

Public Key Cryptography Infographic Cryptography Good Passwords Security

Privacy Preserving Data Mining Ppdm Techniques E2matrix Research Lab Data Data Mining Cryptography

Comaparing Top 4 Cryptocurrencies Cryptopanic Blockchain Cryptocurrency Cryptocurrency Trading Bitcoin Business

Pdf A Survey On The Cryptographic Encryption Algorithms

Download Crypto Logos Icon Pack Available In Svg Png Icon Fonts In 2021 Glyph Icon Icon Pack Glyphs

Bitcoin S 12th Birthday Btc Pushes Above 14k Shortly On Whitepaper Anniversary Halloween Saturday Journal Bitcoin Thoughts

Register Pivot To Get Free Daily Btc Bitcoins Bonus Pivot Is A Community For Cryptocurrency Investors Http Blockchain Blockchain Cryptocurrency Cryptocurrency

In Other Words Running Software That Cracks Cryptographic Puzzles And Rewards You With Coins For Solving The Puzzle Mining Is How Transactions Get Added To Th
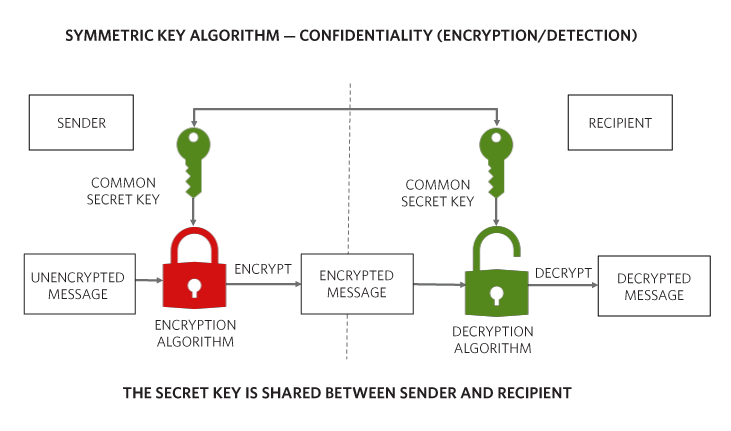
Cryptography Fundamentals On The Modern Approach

What Are The Advantages And Disadvantages Of Bitcoins Btc Wonder Bitcoin Cryptocurrency Investing In Cryptocurrency


Posting Komentar untuk "Cryptographic K-anonymity"